The Right Secure Hardware for your IoT Deployment
February 18, 2019Announcing new options for SQL Server 2008 and Windows Server 2008 End of Support
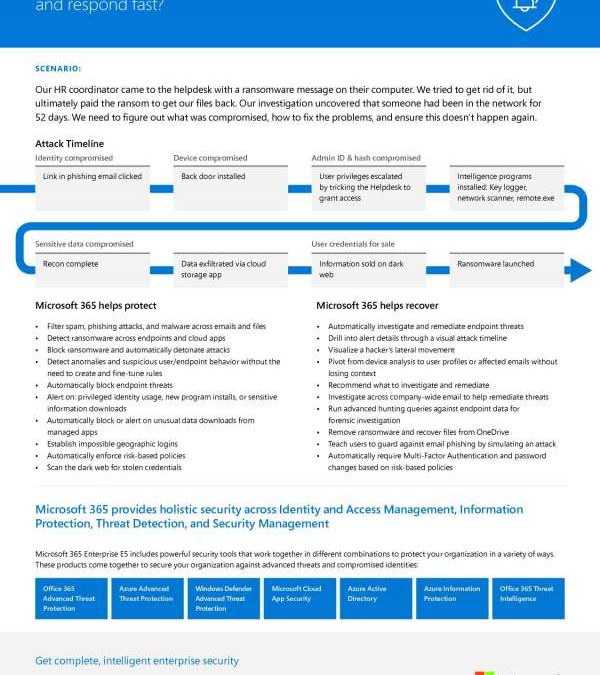
February 19, 2019An all too familiar scenario: A single click in a phishing email and hackers are into a network, resulting in a ransomware request and an uneasy feeling. Learn what tools Microsoft 365 E5 has in its arsenal to ensure this isn’t you.
View: A breach is inevitable. How can Microsoft help me detect and respond fast?