DATA RISK INTELLIGENCE
DO YOU KNOW HOW ATTACKERS ACCESS YOUR DATA?
DO YOU KNOW WHERE YOUR DATA IS LOCATED AND WHO HAS ACCESS TO IT?
DO YOU KNOW WHAT DATA IS AT RISK?
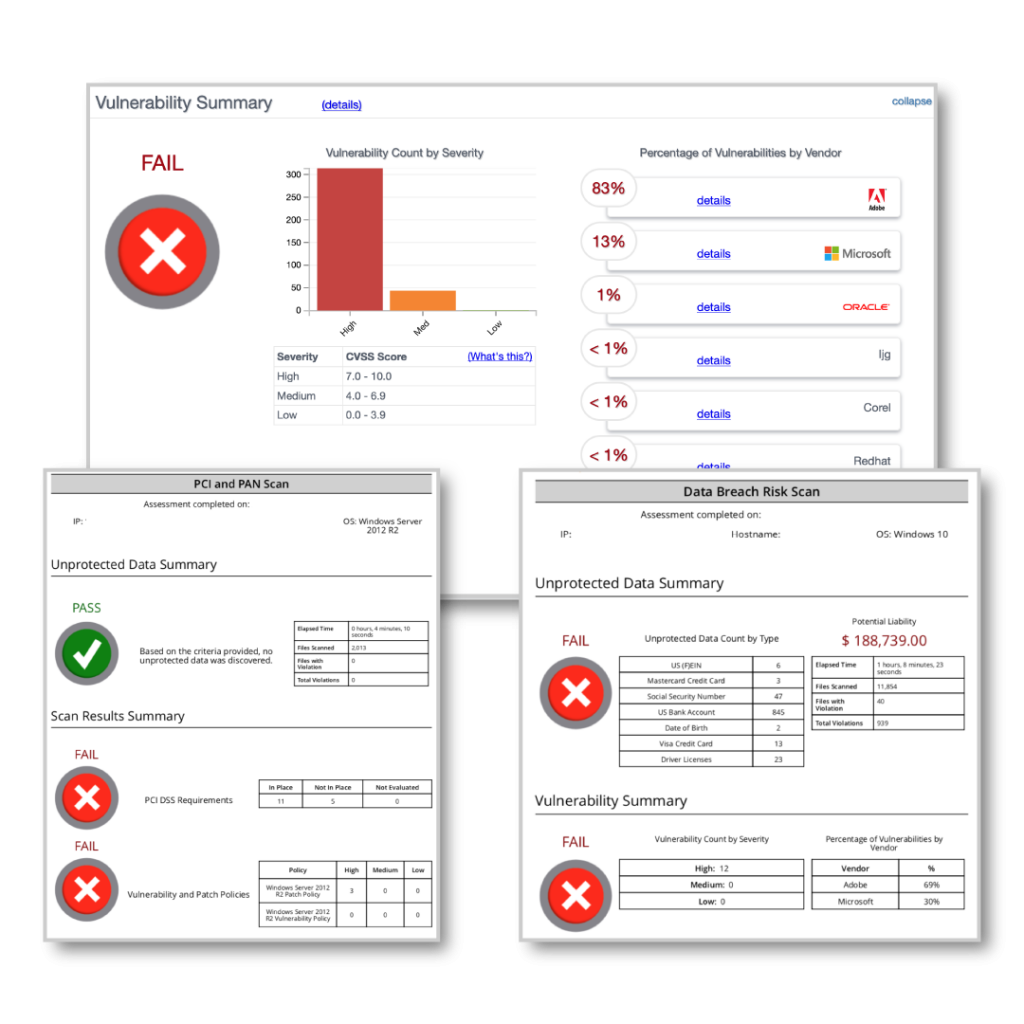
LOCATE AND CONSOLIDATE YOUR DATA AT RISK
Finding and consolidating lots of threat data can be very time consuming, making it difficult to present your data risk to the Board in a way that they can fully understand.
We fix both of those dilemmas.
Digital6’s Data Risk Intelligence service scans for unsecured data across your network—even in persistent storage—and provides an estimated financial figure for your organization’s potential liability in the event of a data breach.
KNOW WHAT DATA IS AT RISK
We identify virtually any type of data – from social security and driver’s license numbers to bank accounts and intellectual property.
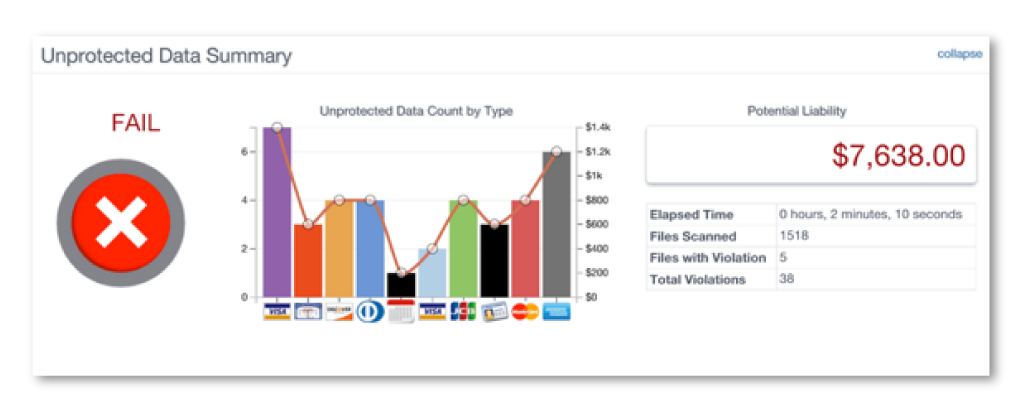
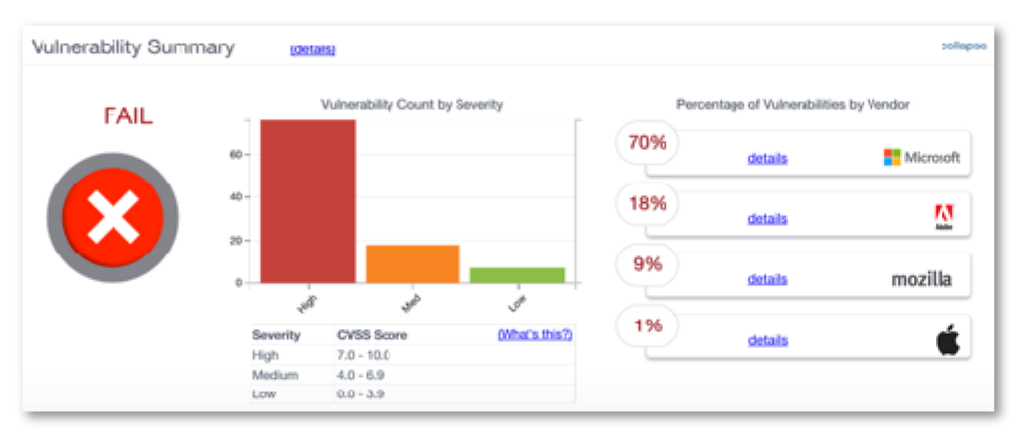
KNOW HOW ATTACKERS ACCESS YOUR DATA
Identify vulnerabilities by vendor and the severity level of each. Groupings make it clear which vulnerabilities should be addressed first. Drill-down details provide specifics about the vulnerability.
KNOW WHERE YOUR DATA IS
AND WHO HAS ACCESS TO IT
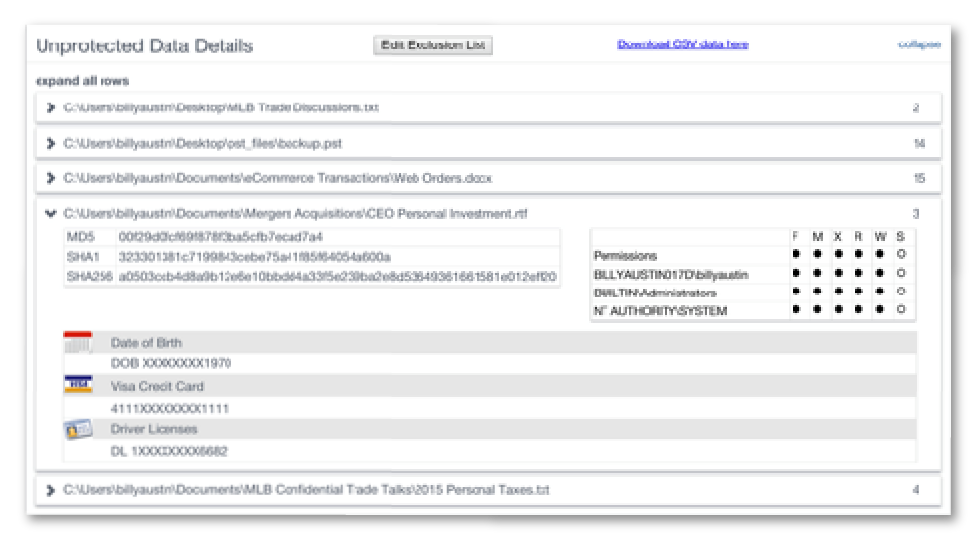
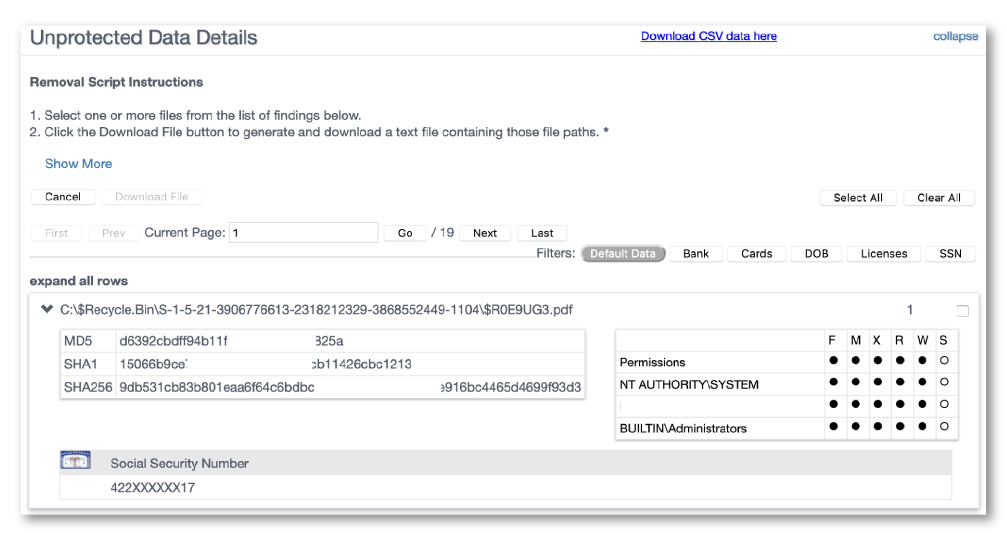
Which file are those credit card numbers stored in? Where are the bank accounts listed? Our report shows you where the sensitive data is lurking, and also who has access to it.
PRESENT
PRIORITIZE
MEASURE
AUDIT
KNOW WHERE AND ON WHAT ASSETS
YOUR SENSITIVE DATA IS LOCATED:
- Confidential corporate documents (Intellectual property, trade data)
- Credit card information
- Personal information (SSN, DOB)
- Sensitive documents that have been saved accidentally to user desktop
- Sensitive documents on social media (DropBox etc.)
- File path of where the data was discovered and who has access
- OS & application vulnerabilities providing attackers with a backdoor to the data
Unlike your traditional vulnerability network appliances, this offering is quick and easy to deploy (like a patch)! Our configuration options are extremely flexible and support a wide range of use cases, including IoT and BYoD.
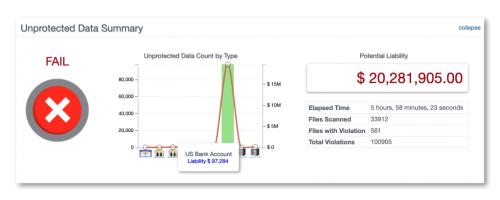
FINANCIAL RISK PROFILE
We assign a dollar value to your risk using analytics gathered from insurance companies and the Dark Web. We give you the intel to track your current posture, security initiatives AND crush your next board meeting.
TRY DATA RISK INTELLIGENCE FREE TODAY
With Stealth Group’s Data Risk Intelligence, you will establish a current view of your risk profile (in $$) – and have the prioritized intel to manage that risk profile down to a target range acceptable to the business.
