Enabling Discovery of Hidden Threats and Rapid Investigations
January 9, 2023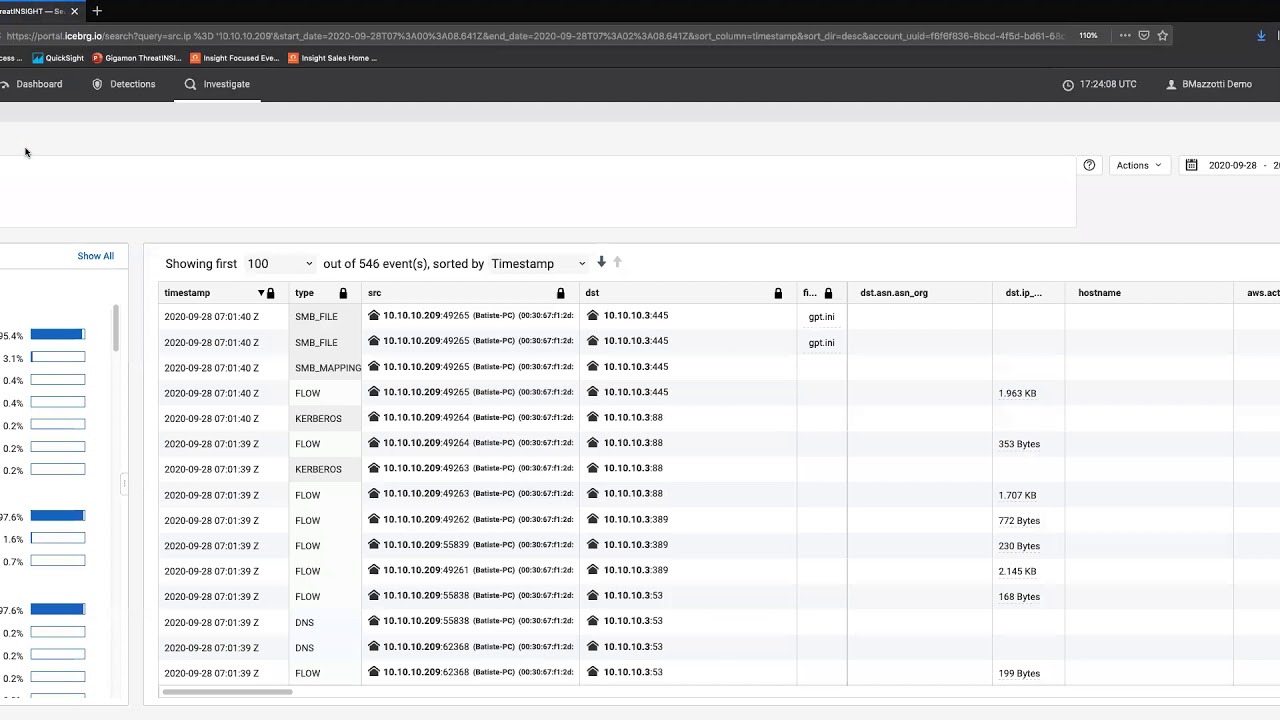
Deep Dive into a Cyber Threat Investigation with ThreatINSIGHT
January 9, 2023Today’s IT teams must look beyond traditional appliance-based security to ensure end users stay productive and assets protected. Download this guide to learn how a unified secure access solution based on zero trust enables you to provide a secure and productive hybrid work environment, modernize IT and promote digital transformation, mitigate risk and prevent cybersecurity threats.
View: Secure Access: A Unified and Cloud-Delivered Zero-Trust Security Solution