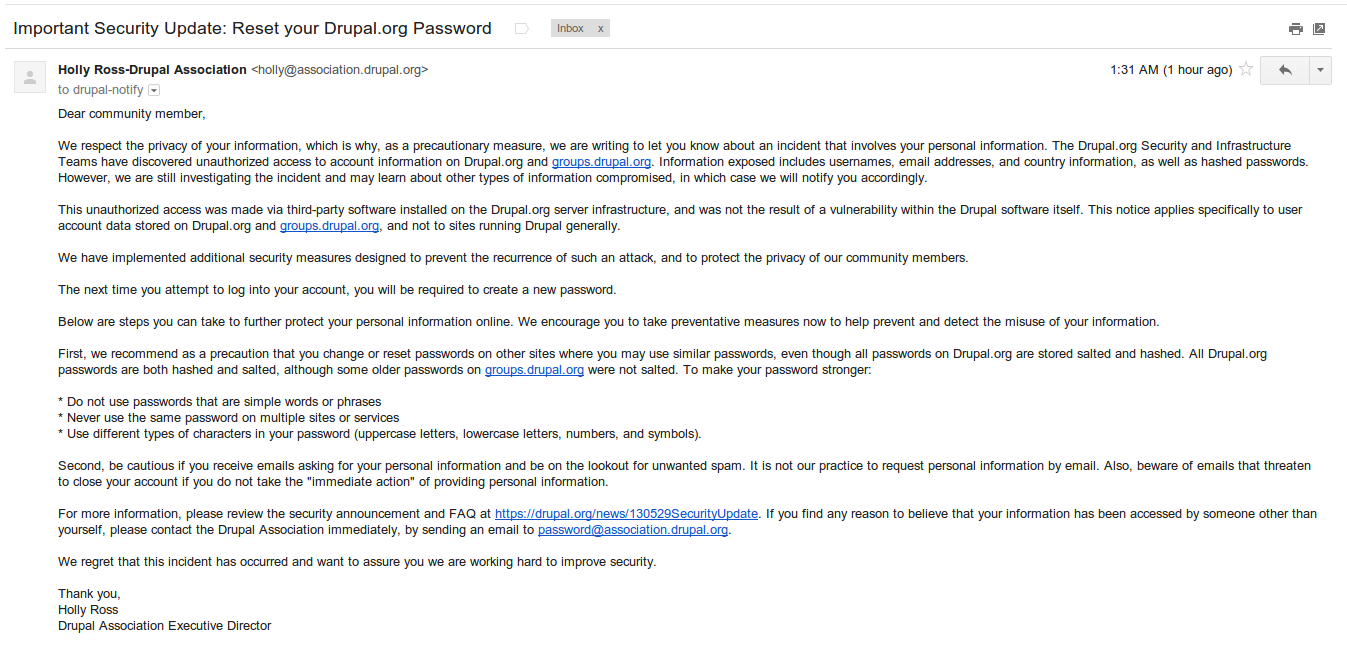
Important Security Update: Reset your Drupal.org Password
May 29, 2013
The Human Side of Security
February 25, 2014 There is a high alert to watch for malformed FileZilla FTP client versions 3.7.3 and 3.5.3.
There is a high alert to watch for malformed FileZilla FTP client versions 3.7.3 and 3.5.3.
As one of the most reliable, free FTP solutions available, even the popular FileZilla technology is not immune to malware. An algorithm, which is part of a malformed FileZilla.exe binary, bypasses firewalls and sends stolen log in information to attackers. The operation is fast, quiet and done only once, without searching bookmarks, other files or saved connections.
Once installed, the malware FTP client is difficult to detect, as it appears to function as designed and closely resembles the official version. Phony download URLs are usually the first suspicious signs, as the installer is typically hosted on hacked websites showing fake content. The malware version is smaller than the real one even though it carries two extra DLL libraries which are not part of the real code. Also, it will not install updates, leaving the user vulnerable for a longer period of time.
Notices on the FileZilla website are reminding users the best way to protect a system from any malware is to download only from official, trusted or well-known sites. Avoid downloading software from unlikely looking third party sites or portals using installers that include adware and PUP applications, or sites offering their own downloaders. Access only the official FileZilla website or SourceForge, its official download partner.
Check out the Avast! website for actual screen shots showing a tainted version of the program.
http://blog.avast.com/2014/01/27/malformed-filezilla-ftp-client-with-login-stealer/
