March 25, 2019
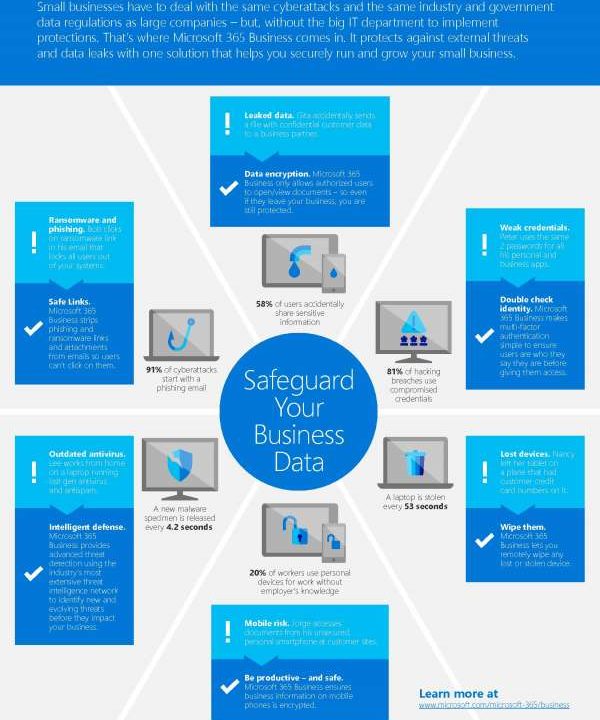
A new malware specimen is released every 4.2 seconds. As a small business owner, how can you be expected to keep up with the ever-shifting threats?
Luckily, you can rely on someone with a bit more resources and experience. Microsoft is continually pulling from their threat intelligence network to stay on top of the latest threats and keep your business protected in the changing landscape.
At Digital6 Technologies, we want to set your business up for success with access to the tools and experience you need to stay protected from threats. Contact us to learn more.